Recent Spanning Tree Protocol (STP) attack:
Attack 1: Taking over the root bridge
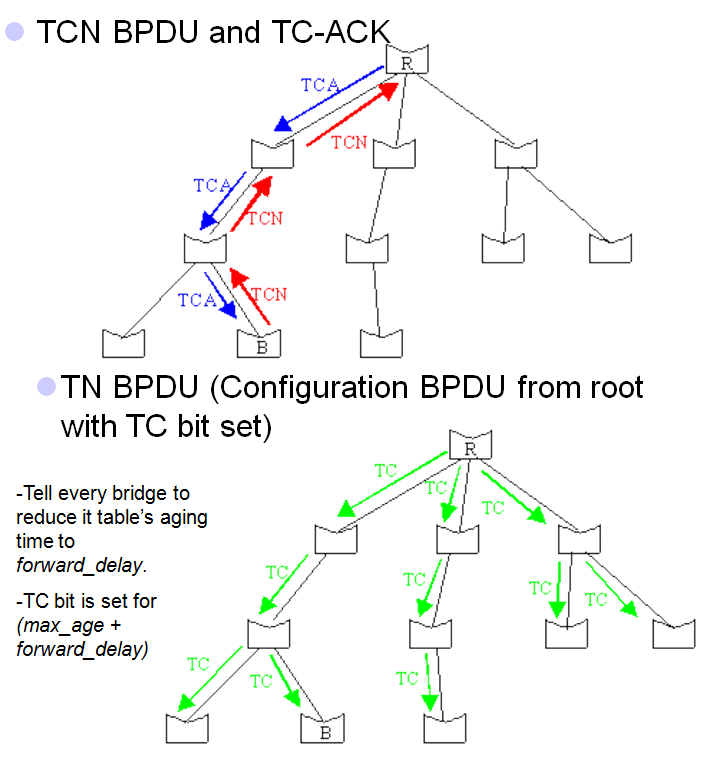
- Never set the TC-ACK bit when receiving TCN BPDUs–> unnecessary flooding
- Keep switching between root bridge and other roles – excessive load on processor
Countermeasures
- Root guard
- BPDU-guard
Root ownership attack countermeasure – Root guard
- Ensures that the port on which root guard is enabled is the designated port. Normally, root bridge ports are all designated ports, unless two or more ports of the root bridge are connected together.
- If the bridge receives superior BPDUs on a root guard-enabled port, root guard moves this port to a root-inconsistent STP state. It is effectively equal to a listening state. No traffic is forwarded across this port.
- Configured on a per-port basis
- May be enabled on all ports where root bridges should not appear
Root ownership attack countermeasure – BPDU-Guard
- Devices behind ports with BPDU-guard enabled are unable to influence the STP topology. Such devices include hosts running Yersinia, for example. At the reception of a BPDU, BPDU-guard disables the port. BPDU-guard transitions the port into the errdisable state, and a message is generated.
- Unlike root guard this disable the ports when any BPDU is received.
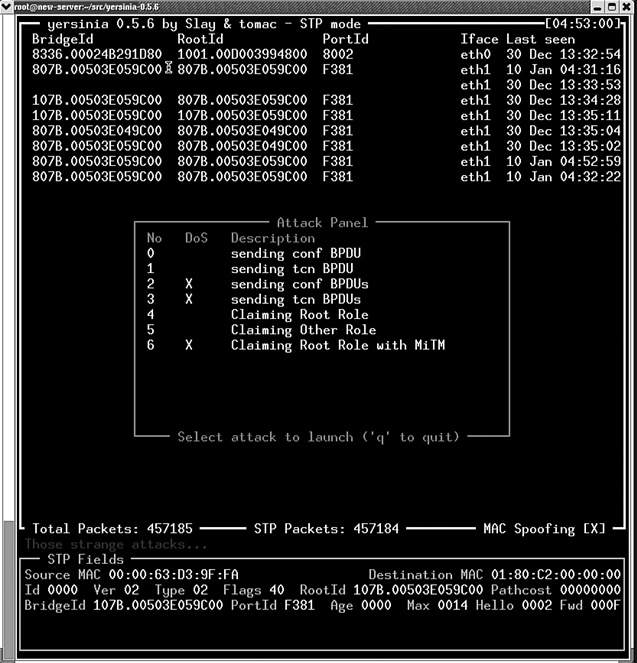
Attack 2 – DoS using a Flood of Config BPDUs
Yesinia can generates approximately 25,000 BPDUs per sec on a test machine (Intel Pentium 4 machine running Linux 2.4-20.8), enough to bring a Catalyst 6500 Supervisor Engine 720 running 12.2(18)SXF to a 99 percent CPU utilization on the switch processor
Countermeasures
- BPDU-guard
- BPDU filtering – disallow BPDUs in both directions. Should only be enabled on workstations facing ports.
- Layer 2 PDU rate limiter
Attack 3 – DoS using a Flood of TCN BPDUs – unnecessary flooding
- BPDU-guard
- BPDU filtering
Attack 4 – Simulating a Dual-Homed Switch
- BPDU-guard
- BPDU filtering
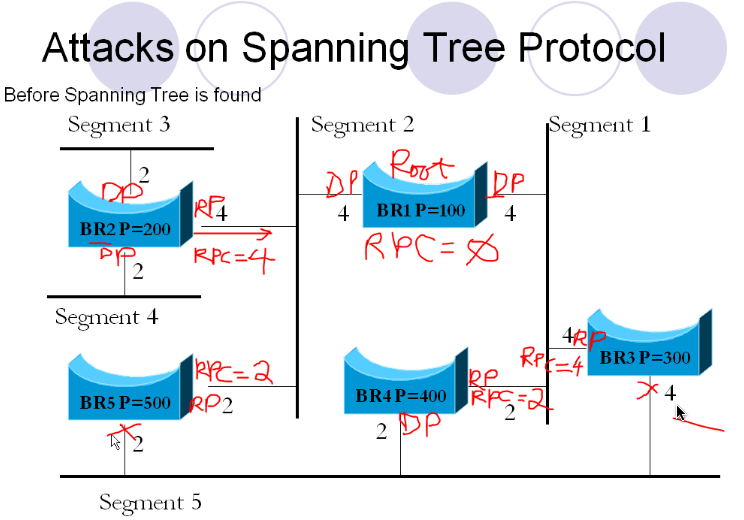
Info on Spanning Tree Protocol
Process
Roles of ports
RPC = Root Path Cost (cost to root switch)
Root Port = Port used to get to root
How do we calculate cost to root?
You only add a cost when you send out on a port. Then that port becomes the new root RPC
Tiebraker – if multiple ports that have same root path cost, you pick the on that has lowest root number
A root should only have destination ports (DP). Ports that are neither a destination or root port should be blocked.
There is a tie braker for the DP on segment 5 (between BR5 and BR4), because BR4 has the lowest port number it wins. The other ports in the segment are dropped from the tree.
Example of calculating a spanning tree:
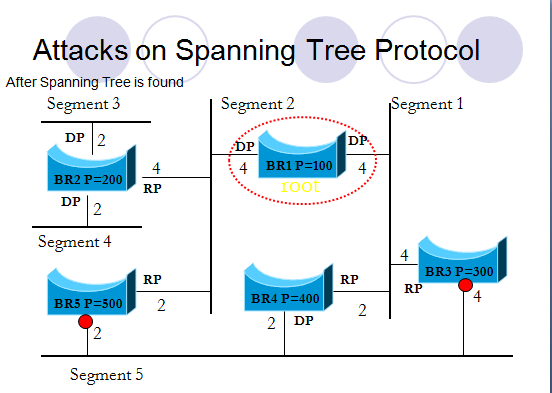
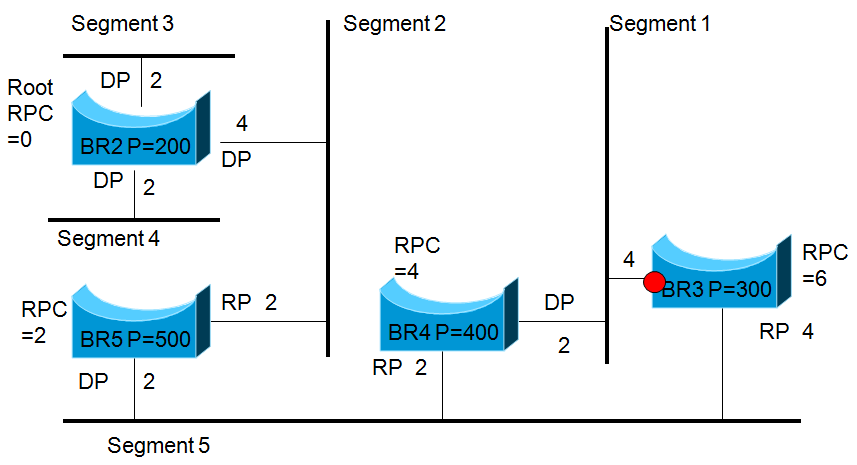
Calculate the new spanning tree after BR1 is down
The first thing you have to do is designate the new root.
We define p=200 as root because “At the base of the tree is a root bridge – The switch with the lowest bridge ID (a concatenation of a 16-bit user-assigned priority and the switch’s MAC address) is elected as the root-bridge.” It has a root cost of 0 and no root ports (as they go to the root).
Which port does p=300 use to get to root? It uses the 4 on the bottom to get to 500 and then 2 to get to 200, total 6, so RPC=6.
Port States
Network-wide timers