Let’s get started detecting streams (ADS)
What is an stream?
An stream is essentially a hidden file within another file (.txt, .jpg, .mp3, .exe, etc)
Why should I care?
Files can contain malicious streams and compromise your machine
Creating an stream
Open up command prompt and run this in a directory
echo 'the password is xxx22' > tst.txt:test.txt
Using FragExt to detect Streams (x86 x64)
FragExt is a great shell extension to detect streams in windows
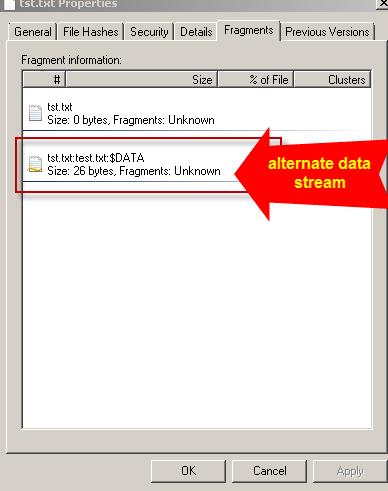
After you install the package there is a new tab in the “properties” window of a file called “Fragments”. This is where streams appear.
Below is an example of an stream i created appearing in the Fragments Tab:
Listing ADS via streams tab in the properties window – The Microsoft way (32bit only)
Download NTFSext.exe from http://download.microsoft.com/download/F/C/6/FC6943EB-790A-44AA-B32D-14ED7E22FD5D/NTFSExt.exe NTFSext.exe contains a DLL file called strmext.dll. Copy this DLL to the system32 folder and run the command
regsvr32 StrmExt.dll
This will create a new tab in the file properties of Windows Explorer. If you suspect that a file has an ADS, you can open its properties windows and check the streams tab which would list any streams attached with the file.
Also copy these to C:\windows\system32
WStreams.vbs and HardLinks.vbs
Demonstrating streams tab
In order to achieve the same for the folders as well, you need to add the following two registry entries by running regedit.exe from the run browser
HKEY_CLASSES_ROOT\Directory\shellex\PropertySheetHandlers\{C3ED1679-814B-4DA9-AB00-1CAC71F5E337} HKEY_CLASSES_ROOT\Drive\shellex\PropertySheetHandlers\{C3ED1679-814B-4DA9-AB00-1CAC71F5E337}
Or create two files in notepad with the following content and save as.reg
file1:
Windows Registry Editor Version 5.00
[HKEY_CLASSES_ROOT\Directory\shellex\PropertySheetHandlers\{C3ED1679-814B-4DA9-AB00-1CAC71F5E337}]
file2:
Windows Registry Editor Version 5.00
[HKEY_CLASSES_ROOT\Drive\shellex\PropertySheetHandlers\{C3ED1679-814B-4DA9-AB00-1CAC71F5E337}]
Then double click the file and add to registry
sources:
http://www.forensicfocus.com/dissecting-ntfs-hidden-streams
http://www.sans.org/reading_room/whitepapers/honors/–streams-shadows-light_1503